Multi-CDN Resilience: Lessons From Real Outages
Earlier this year, I watched closely as Cloudflare experienced a major outage, and separately, Azure Front Door had a rough patch. These weren’t just technical headlines — teams around the world felt the impact on revenue, partner portals, and customer-facing applications.
The takeaway is clear: relying on a single CDN is a single point of failure.
Your digital infrastructure matters and ignoring this risk is no longer an option. That said, understanding how much downtime your business can tolerate is equally important. Not every outage is catastrophic, and risk decisions should be intentional, not accidental.
The Real Entry Point Isn’t Your CDN
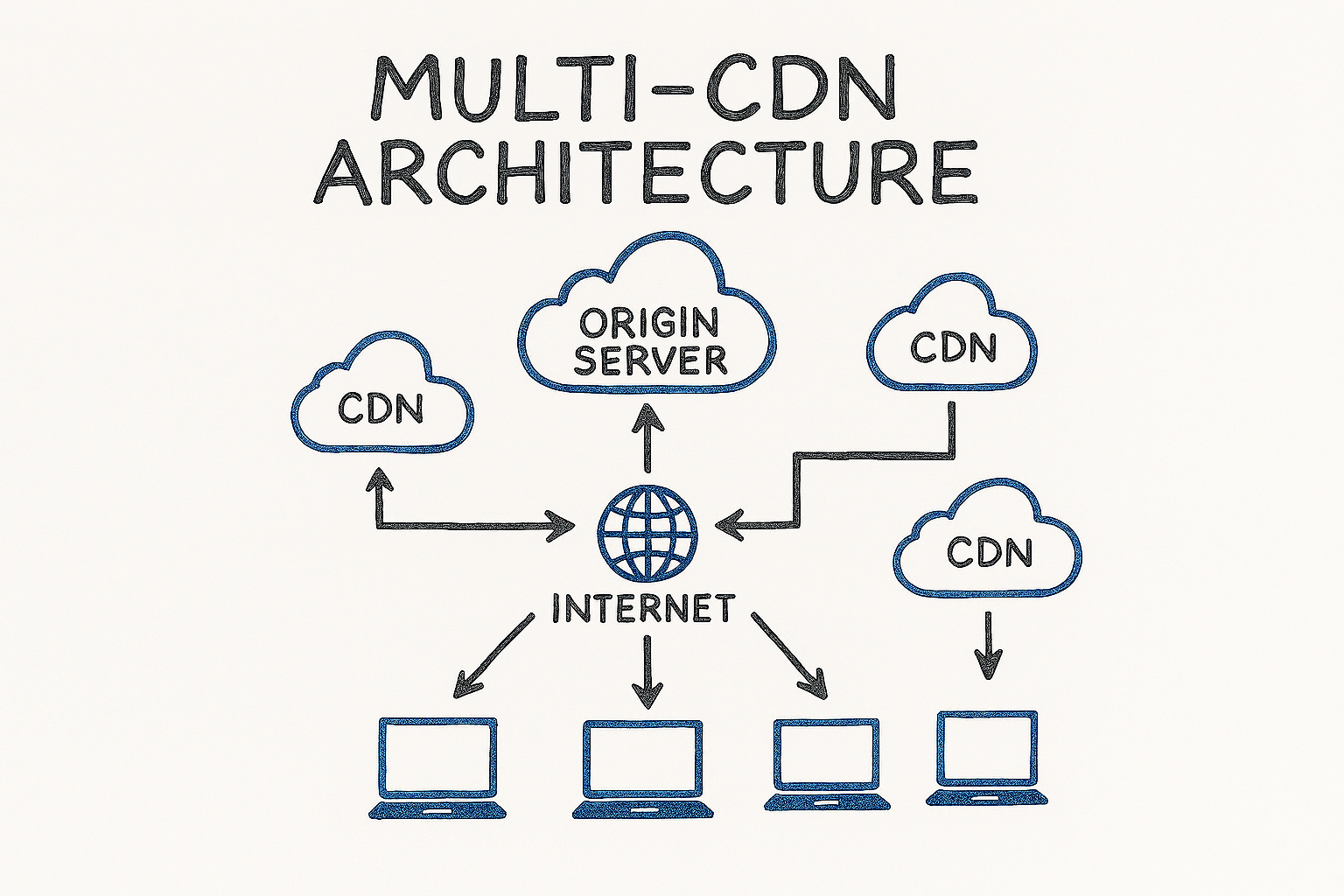
Many assume the CDN is the first point of contact for users. I’ve seen this mistake repeatedly.
Traffic first hits:
- Authoritative DNS
- Global Traffic Management (GTM)
- Health-based routing logic
- The CDN layer
If DNS fails, your site disappears and it doesn’t matter how many CDNs you have in place. Your GTM and DNS strategy define resilience before the CDN even comes into play.
Why Multi-CDN Makes a Difference
1. Business Continuity
When one CDN experiences:
- POP outages
- WAF propagation delays
- Control-plane instability
- Regional routing issues
A multi-CDN setup can shift traffic automatically. No manual intervention, and for critical systems, no revenue pause.
For less critical services, some downtime may be acceptable but the key is knowing which systems need full redundancy and which can tolerate brief interruptions.
2. Smarter Performance Across Regions
Not all CDNs perform equally everywhere. Some excel in APAC, others in the Middle East or Europe.
A GTM that understands these regional differences can:
- Route Middle East users via Provider A
- Route APAC users via Provider B
- Adjust EU traffic dynamically based on real-time latency
Performance becomes measurable and actionable, rather than just theoretical.
3. Security Diversity
Each CDN has its own:
- WAF engine
- Bot mitigation signatures
- DDoS infrastructure
- Control plane
A misconfiguration or security gap in one provider does not compromise your entire digital presence. This approach gives a layer of safety and reduces systemic risk.
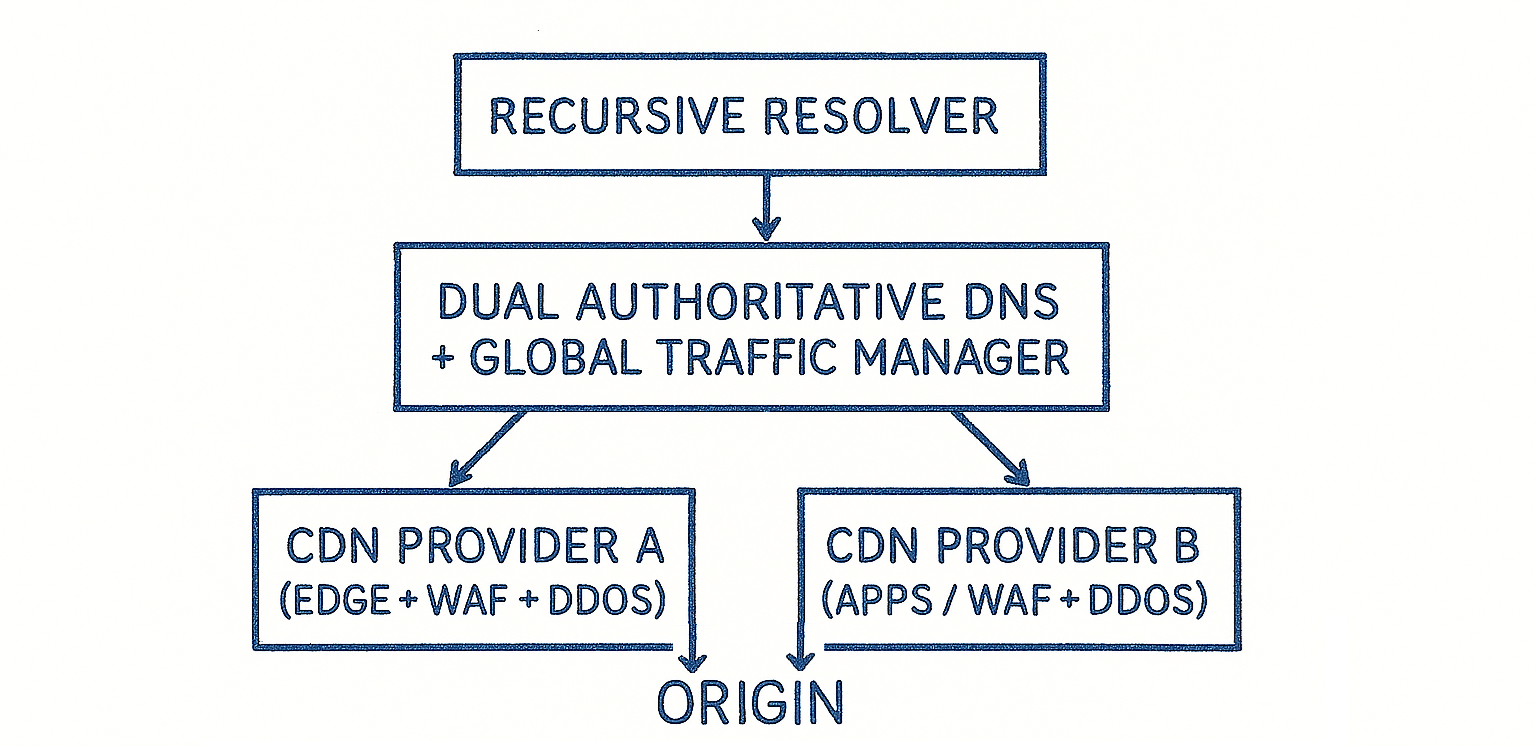
Reference Architecture
Implementation Principles
1. Dual DNS Providers
Avoid tying DNS and CDN exclusively to the same provider. Independent authoritative DNS providers reduce systemic risk and allow controlled failover.
2. Real-Time Health Monitoring
Your GTM should:
- Run active health checks
- Measure latency continuously
- Adjust DNS answers dynamically
Keep TTLs short (20–60 seconds) to enable fast failover. The goal is resilience where it matters most, not blanket zero-downtime across everything.
3. Unified Observability
Aggregate logs from all CDNs into a central analytics platform for:
- SLA validation
- Security anomaly detection
- Performance benchmarking
Understanding how traffic flows and where bottlenecks occur lets you make informed business decisions not just reactive tech fixes.
Final Thoughts: Designing for Failure with Business Context
Digital resilience isn’t optional anymore. Multi-CDN with redundant DNS and smart traffic routing is now a core architectural decision.
From experience, teams that assume everything will always work are the ones scrambling during outages. Teams that plan for failure? They stay online, keep customers happy, and protect revenue even when the unexpected happens.
At the same time, not all downtime is catastrophic. Some systems can tolerate brief interruptions depending on business priorities. For example, low-traffic maintenance windows or non-critical applications. The key is intentional decision-making: balancing risk, cost, and customer impact, rather than chasing a perfect but impractical zero-downtime goal.